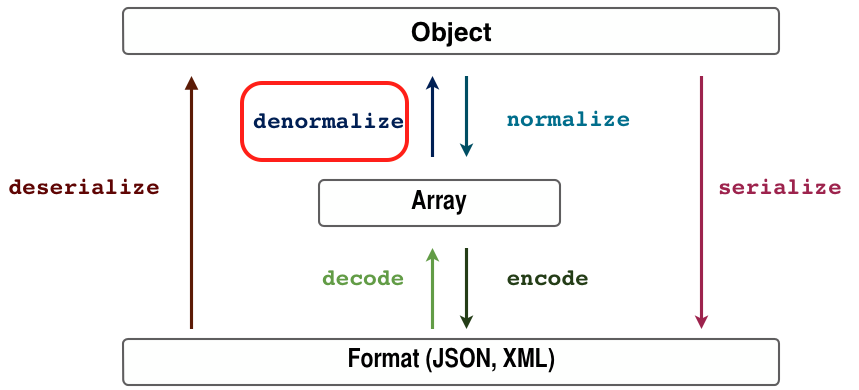
Denormalization Context
Maintenant que nous savons ce que nous exposons en lecture nous voulons définir ce que nous voulons sur l'écriture.
Nous utiliserons le groupe de denormalization user:write
/**
* @ORM\Entity(repositoryClass=UserRepository::class)
* @ApiResource(
* normalizationContext={"groups"={"user:read"}},
* denormalizationContext={"groups"={"user:write"}},
* )
*/
class User implements UserInterface
// ...
/**
* @ORM\Column(type="string", length=180, unique=true)
* @Groups({"user:read", "user:write"})
*/
private $email;
/**
* @var string The hashed password
* @ORM\Column(type="string")
* @Groups({"user:write"})
*/
private $password;
Assertions pour email
Nous allons également ajouter les assertions car nous voulons nous assurer que notre email est un email valide et que notre mot de passe soit sécurisé et contienne certain caractères.
use Symfony\Component\Validator\Constraints as Assert;
// ...
/**
* @ORM\Column(type="string", length=180, unique=true)
* @Groups({"user:read", "user:write"})
* @Assert\NotBlank()
* @Assert\Email()
* @Assert\Length(max="180")
*/
private $email;Dorénavant si nous n'envoyons pas un email correct nous aurons l'erreur suivante
{
"@context": "/api/contexts/ConstraintViolationList",
"@type": "ConstraintViolationList",
"hydra:title": "An error occurred",
"hydra:description": "email: This value is not a valid email address.",
"violations": [
{
"propertyPath": "email",
"message": "This value is not a valid email address.",
"code": "bd79c0ab-ddba-46cc-a703-a7a4b08de310"
}
]
}Et si nous n'envoyons pas la clé email dans le payload nous aurons l'erreur suivante :
{
"@context": "/api/contexts/ConstraintViolationList",
"@type": "ConstraintViolationList",
"hydra:title": "An error occurred",
"hydra:description": "email: This value should not be blank.",
"violations": [
{
"propertyPath": "email",
"message": "This value should not be blank.",
"code": "c1051bb4-d103-4f74-8988-acbcafc7fdc3"
}
]
}Assertions pour le mot de passe
Voici les assertions qui attendent qu'un mot de passe ait au minimum 8 caractères, qu'il doit comporter une majuscule, une minuscule, un chiffre et un caractère spécial.
/**
* @ORM\Column(type="string")
* @Groups({"user:write"})
* @Assert\Length(
* min = 8,
* max = 32,
* minMessage = "Your password must be at least {{ limit }} characters long",
* maxMessage = "Your password cannot be longer than {{ limit }} characters"
* )
* @Assert\Regex(
* "/^.*(?=.{8,})((?=.*[!@#$%^&*()\-_=+{};:,<.>]){1})(?=.*\d)((?=.*[a-z]){1})((?=.*[A-Z]){1}).*$/",
* message = "Your password needs an uppercase, a lowercase, a digit and a special character"
* )
*/
private $password;Si on envoie un mot de passe qui ne contient pas les validations attendues nous avons la liste des violations qui est retourné. Exemple avec "password": "$"
{
"@context": "/api/contexts/ConstraintViolationList",
"@type": "ConstraintViolationList",
"hydra:title": "An error occurred",
"hydra:description": "password: Your password must be at least 8 characters long\npassword: Your password needs an uppercase, a lowercase, a digit and a special character",
"violations": [
{
"propertyPath": "password",
"message": "Your password must be at least 8 characters long",
"code": "9ff3fdc4-b214-49db-8718-39c315e33d45"
},
{
"propertyPath": "password",
"message": "Your password needs an uppercase, a lowercase, a digit and a special character",
"code": "de1e3db3-5ed4-4941-aae4-59f3667cc3a3"
}
]
}Commentaires
Connectez-vous pour laisser un commentaire